Why it matters: A simple search on Amazon or any other online retailer will show that consumers have a wide selection of USB-C cables, with options ranging from just a few dollars to over $100. The price primarily depends on things like length, quality of construction, compliance with various parts of the USB-C spec, and branding.
While USB-C may be the most flexible connection for digital devices, it's also confusing to the point where it pays off to learn about the intricacies of this ever-evolving standard. Its primary goal is to simplify things so consumers can use a single cable for data, audio, video, and power delivery.
However, a cable's specs are not always the same, and packing is often vague regarding the cable's capabilities. There is also the potential for USB-C cables to hide malicious circuitry that compromises the security of your device.
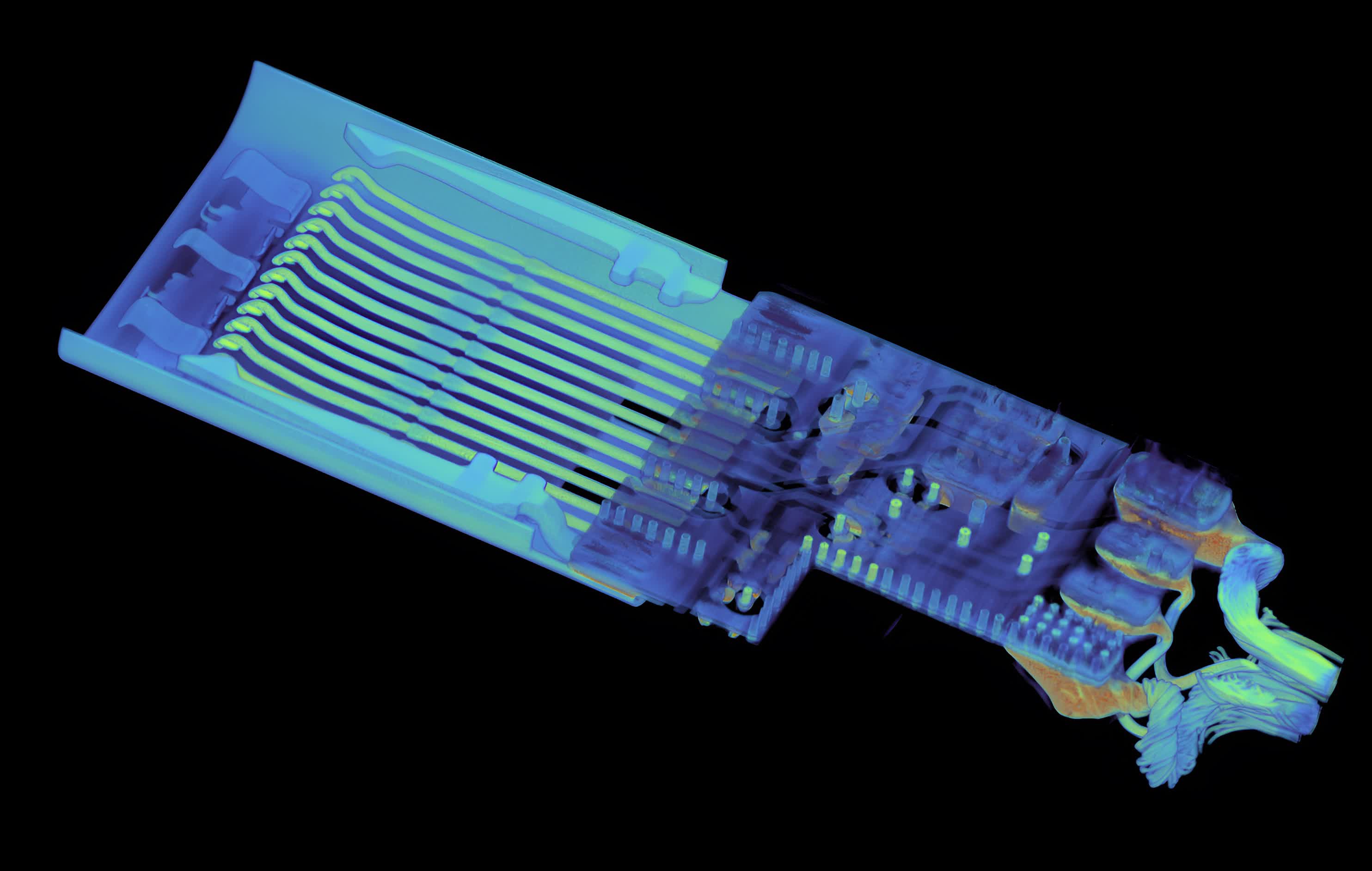
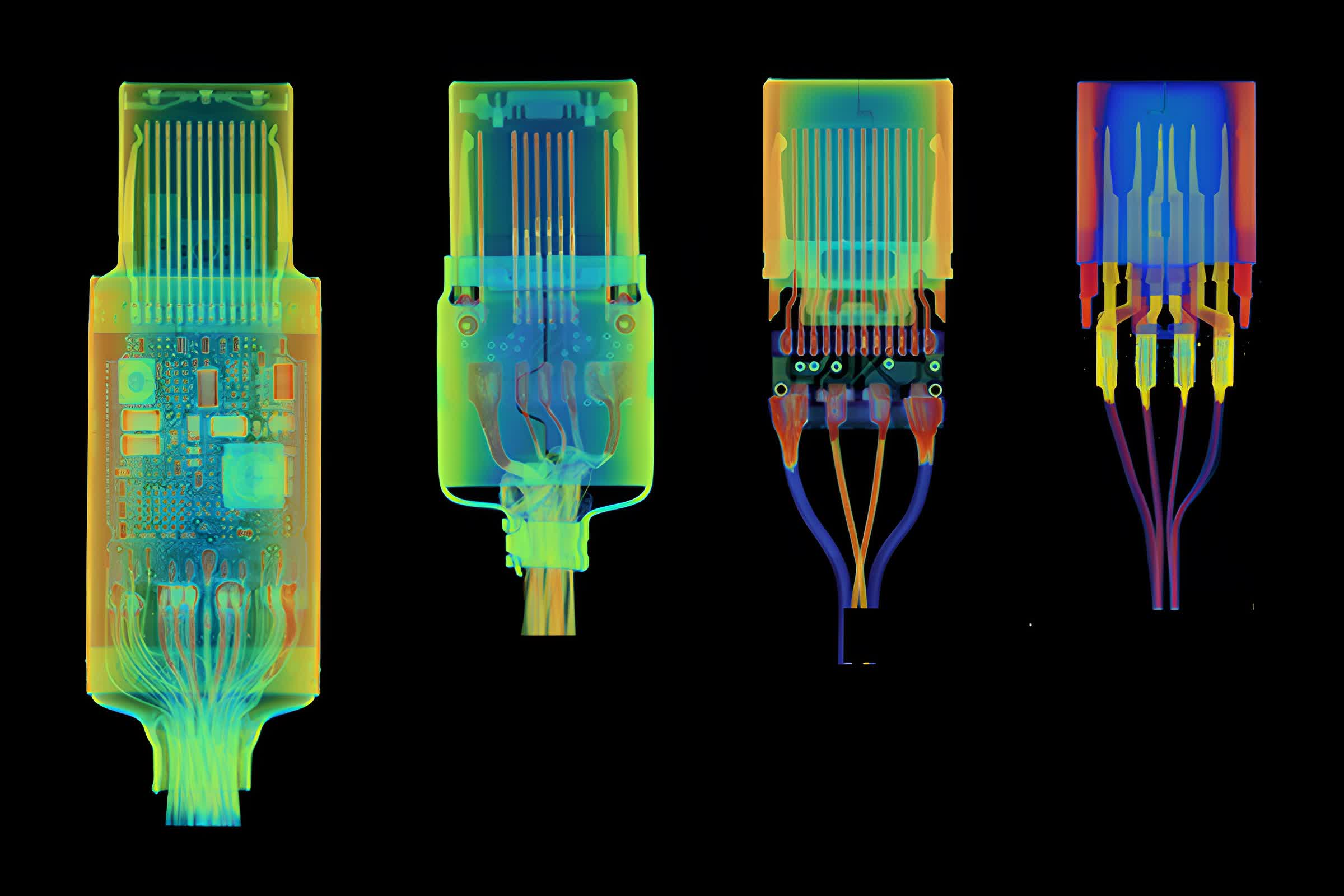
At first glance, USB-C cables look mostly the same. However, some feature active circuitry inside. Thanks to equipment like Lumafield's Neptune Industrial X-Ray CT Scanner, we can see the internal design of something like Apple's $129 Thunderbolt 4 USB-C cable is much more complex than a $11.69 Amazon Basics cable, which doesn't even use all the pins on the USB-C connector (below).
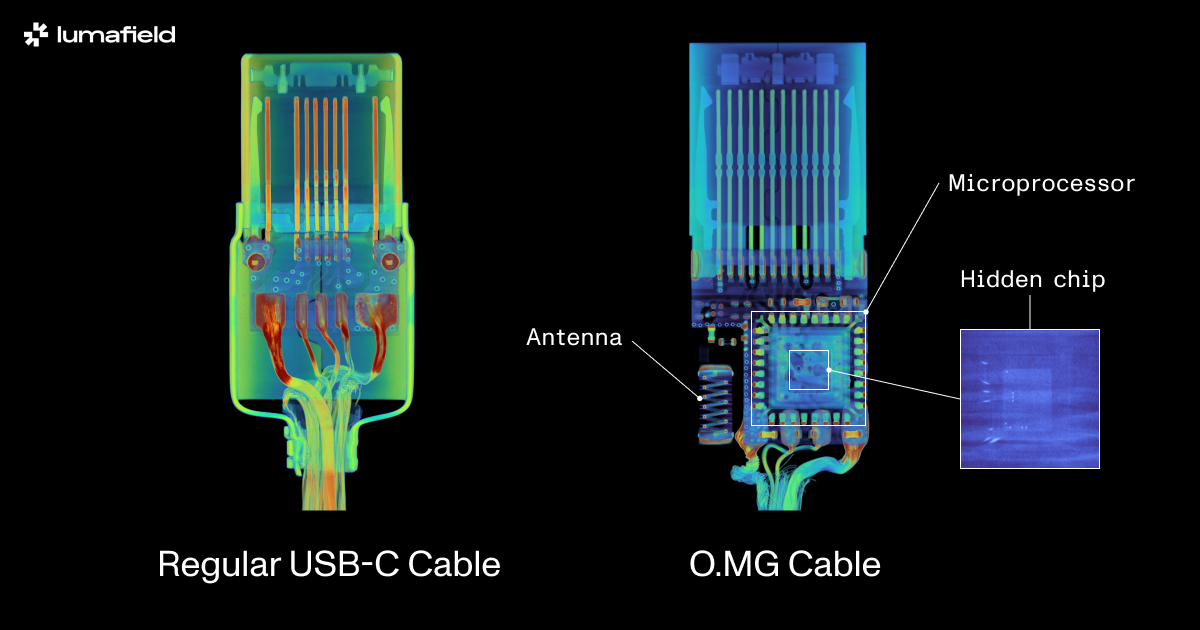
More recently, Lumafield investigated an O.MG USB-C cable. It is another example of the sophisticated electronics you can hide inside a normal-looking USB-C connector. However, the O.MG cable is a niche product created by Mike Grover and designed for security research and to increase awareness about potentially malicious hardware users could find in the wild.
John Bruner of Lumafield says that many people who saw the previous scans were understandably worried that what looks like an ordinary USB connector could easily contain hardware that can inject malicious code, log keystrokes, and extract personal data.
This looks like an ordinary USB-C connector, but when we CT scan it, we find something sinister inside…🧵 pic.twitter.com/Q1RfpnS0Sp
– Jon Bruner (@JonBruner) December 4, 2024
Notably, the O.MG cable features a clever design that could make it easy to overlook such circuitry when using standard inspection methods. While an ordinary 2D X-ray scan would quickly reveal the antenna and microcontroller, it took a 3D scan and fiddling with visualization parameters to spot a second set of wires going to a second die stacked on top of the microcontroller (below).
Bruner believes CT scanning is quickly becoming an important security tool for verifying the integrity of hardware during manufacturing before it has a chance of causing harm to individuals, companies, and critical infrastructure. An undetected supply chain attack can lead to serious consequences, as shown by the recent example of exploding pagers used in Lebanon to target Hezbollah leaders.
Fortunately, the average consumer doesn't need to worry about explosives inside their cables, and products like the O.MG cable are usually too expensive for the general public, with these specialty devices going for up to $200. Even the EvilCrow Wind cable, a more affordable alternative that hides a powerful ESP32-S3 SoC with Wi-Fi and Bluetooth connectivity, still costs over $60.
Still, Bruner recommends using certified USB-C cables and avoiding public USB charging ports when possible.
A USB-C cable can hide a lot of malicious hardware, CT scan shows